Network Slicing In 5G Network
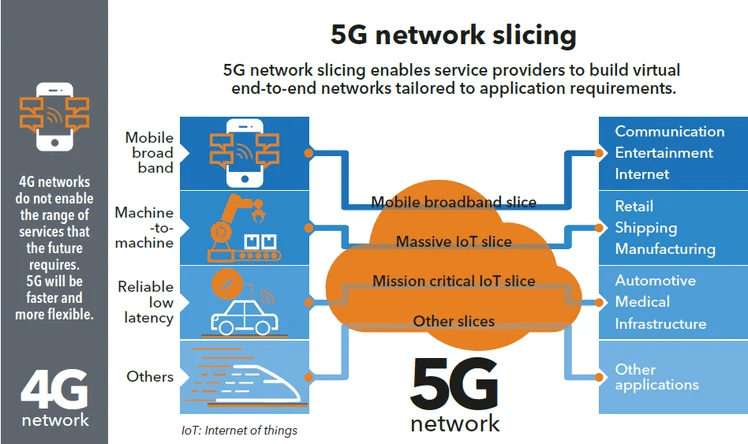
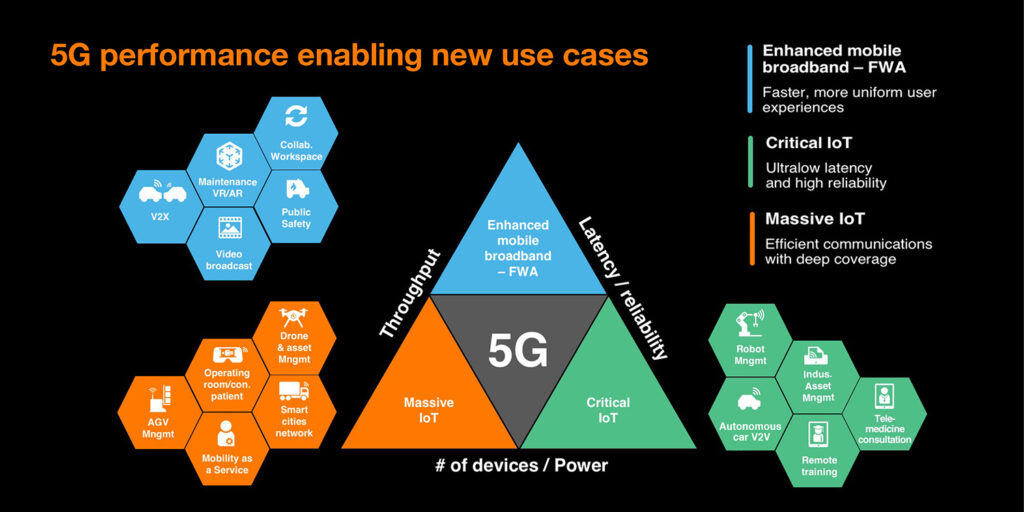
Introduction to Network Slicing in 5G Networks 5G Network Virtualization is a groundbreaking technology that allows the creation of multiple virtual networks on a shared physical infrastructure. Each slice can be customized to meet specific requirements, providing tailored services for different applications and industries. Think of it as having different lanes on a highway, each dedicated to different types of traffic, ensuring smooth and efficient travel for all. Network slicing in 5G networks revolutionizes connectivity by enabling more efficient and flexible use of network resources. Overview of 5G Network Slicing The Evolution from 4G to 5G The shift from 4G to 5G networks is more than just an increase in speed. While 4G networks offered faster internet compared to previous generations, they struggled to support the growing diversity of connected devices and applications. 5G networks, with the help of network slicing, address these limitations by offering a more flexible, efficient, and scalable solution. This enables enhanced mobile broadband, ultra-reliable low-latency communication, and massive machine-type communication, all within the same infrastructure of 5G Network Virtualization. Technical Overview of Network Slicing 5G Network Virtualization is made possible through two key technologies: Software-Defined Networking (SDN) and Network Function Virtualization (NFV). SDN separates the control and data planes, allowing centralized and programmable management of the network. NFV, on the other hand, virtualizes network functions so they can run on standard hardware, providing flexibility and scalability. Together, these technologies enable operators to create and manage multiple virtual networks on a single physical network, each optimized for different services. How Network Slicing Works Creating network slices involves several steps: This process allows network slicing in 5G networks to deliver dedicated resources and optimized performance for each application or service. Benefits of Network Slicing in 5G 5G Network Virtualization offers numerous benefits: Use Cases of Network Slicing Network slicing in 5G networks is versatile and supports various use cases: Challenges and Considerations While network slicing in 5G networks offers significant advantages, it also presents challenges: Future of Network Slicing The future of network slicing in 5G networks is promising, with continuous advancements on the horizon. Artificial intelligence (AI) and machine learning (ML) are expected to play significant roles in automating slice management and optimization. As technology evolves, we can anticipate even greater efficiency, security, and flexibility in network slicing, paving the way for innovative applications and services. Conclusion Network slicing in 5G networks is set to revolutionize mobile communications. By enabling the creation of multiple, customized virtual networks, it offers unparalleled flexibility and efficiency, supporting a diverse range of applications and services. As we move forward, network slicing will continue to shape the future of connectivity, driving technological advancements and transforming industries. Home – IT solutions (rdmtech.in)
Network Slicing In 5G Network Read More »